Gate.io PoR
Latest audit time:
(UTC+0)
Excess reserve value:
$ B
Algorithm:
Merkle Tree + zk-SNARKs
Total reserve rate:
Merkle Root Hash:
Customer Net Balance
$
Gate Wallet Balance
$
Excess reserve value
$

Not Data
What is 100% Proof of Reserves?
A centralized trading platform manages a ledger for recording user assets in a database. As such, platforms face the challenge of proving that they have full custody of all users' assets in good condition.
Gate.io implemented the Merkle tree to resolve this issue, by storing the hash value of each user's account assets in the leaf nodes of the Merkle tree. Every user can audit the total amount of users' assets stored in the leaf nodes of the Merkle tree and verify whether his funds are included through a qualified third-party audit agency.
If the assets stored in the Merkle tree are verified to be greater than or equal to 100%, it means the users' assets are kept in full on the platform, i.e. the platform provides 100% Proof of Reserves for the users' assets.
Why is the 100% Proof of Reserves so important?

How do we manage to maintain 100% level of reserves?
If the total number of tokens managed by the exchange on the blockchain meets or exceeds the aggregate balance of all user accounts, as captured in a snapshot, the platform maintains a 100% margin for those tokens
Ownership over the wallet
When you use hot or cold wallets, you transfer a randomly designated amount to the addresses designated by the audit company to prove your ownership over the wallet.
The audit company will add up the balance of the relevant addresses to calculate the total amount involved in the transaction (including users' assets and self-owned assets of the platform).
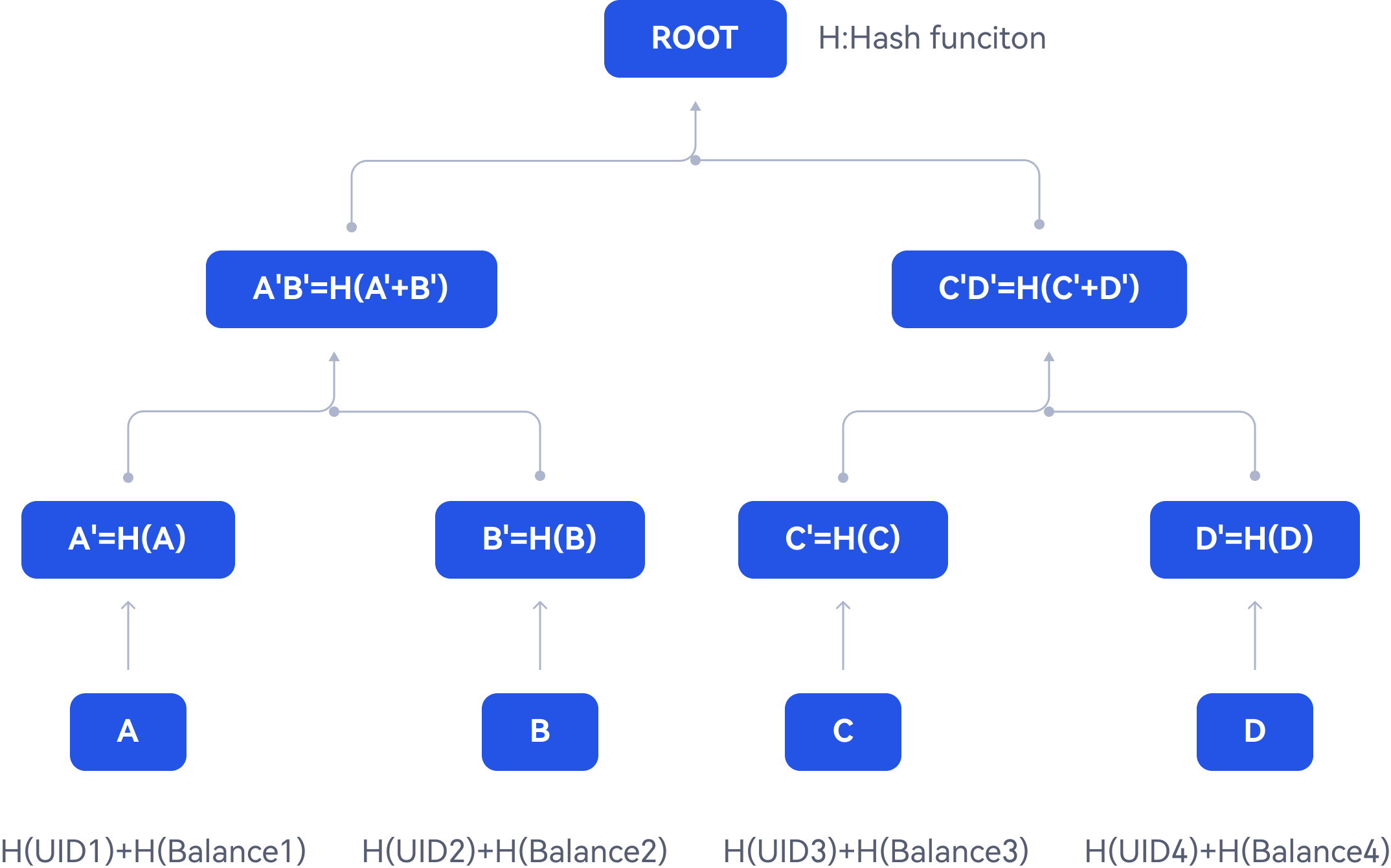
How to build the Merkle tree with hashed user id and user balance?
The hashed user id (UID) and user balances are first exported from Gate's database.
Each pair of hashed UID and user balances will be hashed respectively and then concatenated to form the underlying data block.
For each data block, the same hash function will be applied to generate the leaf nodes of the Merkle tree. The resulting hashed data are subsequently hashed together in pairs to create the parent nodes of the leaf nodes.
This process continues until it results in a single hash known as the merkle root.
Please refer to the diagram below for illustration. After the merkle tree is successfully built, the leaf nodes will be exported into a plain text file, which will be published together with the merkle root hash by the auditor.
What is a Merkle Tree?
In cryptography and computer science, a hash tree or Merkle tree is a tree in which every leaf node is labeled with the cryptographic hash of a data block. Every non-leaf node is labeled with the hash of the labels of its child nodes. Hash trees allow efficient and secure verification of the contents of large data structures.
How do we use a Merkle Tree to provide Proof of Reserves?
We save the hash value of each user's account asset as a leaf node in the Merkle Tree. Then, we employ zk-SNARK technology to confirm that we hold all of the users' assets in full. Throughout this process, no asset data is disclosed. The steps for verification are as follows:
1. zk-SNARK assists in auditing that the total balance of users' assets is stored as leaf nodes in the Merkle Tree (i.e., user account balance). For each leaf node, we confirm the following points:
a. The total amount of assets managed by the platform includes the total asset balance of all users.
b. The net balance of each user is greater than or equal to zero.
c. Change of any user's assets will result in alteration of the Merkle root hash value.
2. User verification: Users can verify the authencity of the proof by verifying the Merkle root hash value using zk-SNARK. The technology enables us to complete the 100% reserve audit in an efficient and safe manner while avoiding the risks of privacy or trade secret leaking, which will help to deliver our commitment to transparent operations and enhance customers' trust.
What are zk-SNARKs?
zk-SNARK, standing for Zero-Knowledge Succinct Non-Interactive Argument of Knowledge, is a groundbreaking tool rooted in cryptography. Utilizing advanced mathematical algorithms, it can proficiently validate the reserve amount without disclosing specific asset details. zk-SNARK not only facilitates swift asset verification but also negates privacy breach risks. Owing to these benefits, coupled with its non-interactive nature and high scalability, it finds extensive applications in areas like on-chain transaction verification, data privacy safeguards, and identity authentication
Verification process.
1. Install the program and download data:
1)Download the verification program:
First, download the verification program via the link provided or access GitHub to download the verification program. Then rename it to main.
2)Download required data:
Access to the Audit Page and locate the batch you need to verify. Click on [Download Merkle Tree] and [Download User Config] to download the data.
Unzip the zkmerkle_cex_xxx.tar.gz compressed file, place the mainprogram inside this folder, and put the user_config.json file inside the config folder.
The program folder is now
zkmerkle_cex_xxx
Config
cex_config.json
user_config.json
proof.csv
zkpor864.vk.save
main
2. Assets verification:
From cmd or terminal, use the cd command to navigate into the downloaded folder, such as cd ~/Downloads/zkmerkle_cex_xxx.
(Before running the program, you might need to execute chmod 777 mainto grant permissions or set security items.)
Execute the following command to begin verification.
./main verify cex
Upon successful verification, the message will be displayed.
All proofs verify passed!!!
For detailed technical documentation and verification principles, please check the GitHub open-source project
Gate.io PoR Implementation

HACKEN
Audit firmAudit time
January 3, 2024
Auditor
Luciano Ciattaglia、Sofiane Akermoun、Nino Lipartiia、Bartosz Barwikowski
Repositories
Audit Report
Gate.io PoR Implementation